感觉整整消失了半年多,回来世界都变了不少
很多没有填的坑变得更大了,而且又生成了很多新的坑
感觉整整消失了半年多,回来世界都变了不少
很多没有填的坑变得更大了,而且又生成了很多新的坑

随手写的,感觉手残了不少
最近在研究棒针和钩针,还是挺有意思的(呸,明显是因为禁止或者暂停做很多事时间太多了![]() )
)
然后就在考虑,那种书上的图解都是怎么做的。
棒针还好,Excel还能凑合
钩针这种360°各种旋转扭曲的就……
然后搜了下github,搜出很多好玩的东西,除了画图解的,还有根据钩针针数生成3D形状的(我用不太遛,针法缩写背不出)
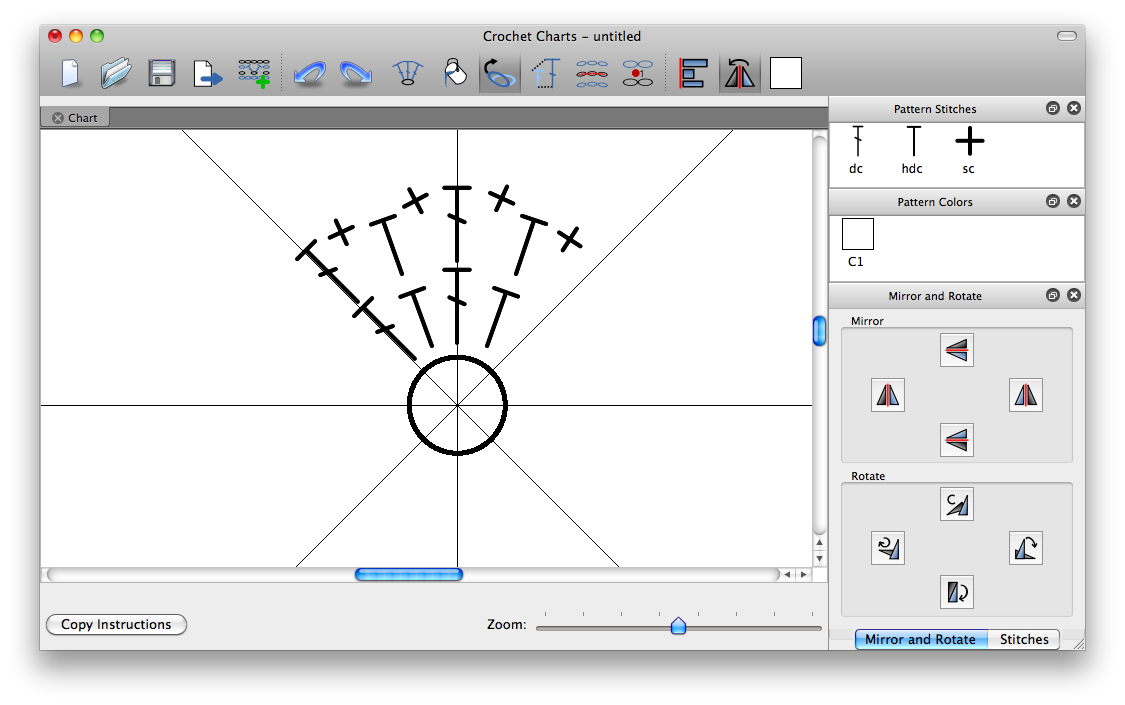
钩针画图解的最顺眼的是这个东西,它自己网址在这里。
Github repo 发现了2个,一个人弄的+hash都一样但是居然没看到Fork痕迹:
https://github.com/iPenguin/CrochetCharts
https://github.com/StitchworksSoftware/CrochetCharts
我最开心的是:支!持!linux!安!装!(虽然还没试)
虽然相比较我们家CDD来说,用起来不是很舒服,但是我很满意了!!!
上回小工具的扩展
最近因为某些那啥的事儿,好多事情都给搁置了,包括学锯子之类的各种事情
今天想动动爪子,不想给某些网站添加流量了
Each character on a computer is assigned a unique code and the preferred standard is ASCII (American Standard Code for Information Interchange). For example, uppercase A = 65, asterisk (*) = 42, and lowercase k = 107.
A modern encryption method is to take a text file, convert the bytes to ASCII, then XOR each byte with a given value, taken from a secret key. The advantage with the XOR function is that using the same encryption key on the cipher text, restores the plain text; for example, 65 XOR 42 = 107, then 107 XOR 42 = 65.
For unbreakable encryption, the key is the same length as the plain text message, and the key is made up of random bytes. The user would keep the encrypted message and the encryption key in different locations, and without both “halves”, it is impossible to decrypt the message.
Unfortunately, this method is impractical for most users, so the modified method is to use a password as a key. If the password is shorter than the message, which is likely, the key is repeated cyclically throughout the message. The balance for this method is using a sufficiently long password key for security, but short enough to be memorable.
Your task has been made easy, as the encryption key consists of three lower case characters. Using cipher.txt (right click and ‘Save Link/Target As…’), a file containing the encrypted ASCII codes, and the knowledge that the plain text must contain common English words, decrypt the message and find the sum of the ASCII values in the original text.
Starting with 1 and spiralling anticlockwise in the following way, a square spiral with side length 7 is formed.
| 37 | 36 | 35 | 34 | 33 | 32 | 31 |
| 38 | 17 | 16 | 15 | 14 | 13 | 30 |
| 39 | 18 | 5 | 4 | 3 | 12 | 29 |
| 40 | 19 | 6 | 1 | 2 | 11 | 28 |
| 41 | 20 | 7 | 8 | 9 | 10 | 27 |
| 42 | 21 | 22 | 23 | 24 | 25 | 26 |
| 43 | 44 | 45 | 46 | 47 | 48 | 49 |
It is interesting to note that the odd squares lie along the bottom right diagonal, but what is more interesting is that 8 out of the 13 numbers lying along both diagonals are prime; that is, a ratio of 8/13 ≈ 62%.
If one complete new layer is wrapped around the spiral above, a square spiral with side length 9 will be formed. If this process is continued, what is the side length of the square spiral for which the ratio of primes along both diagonals first falls below 10%?